 Hire a Tutor
Hire a Tutor 







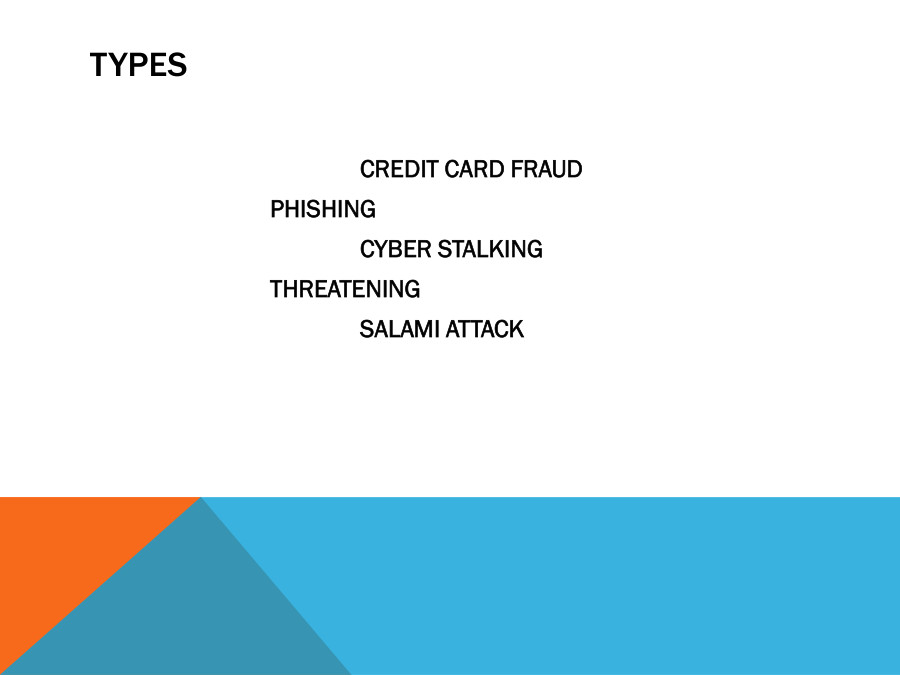









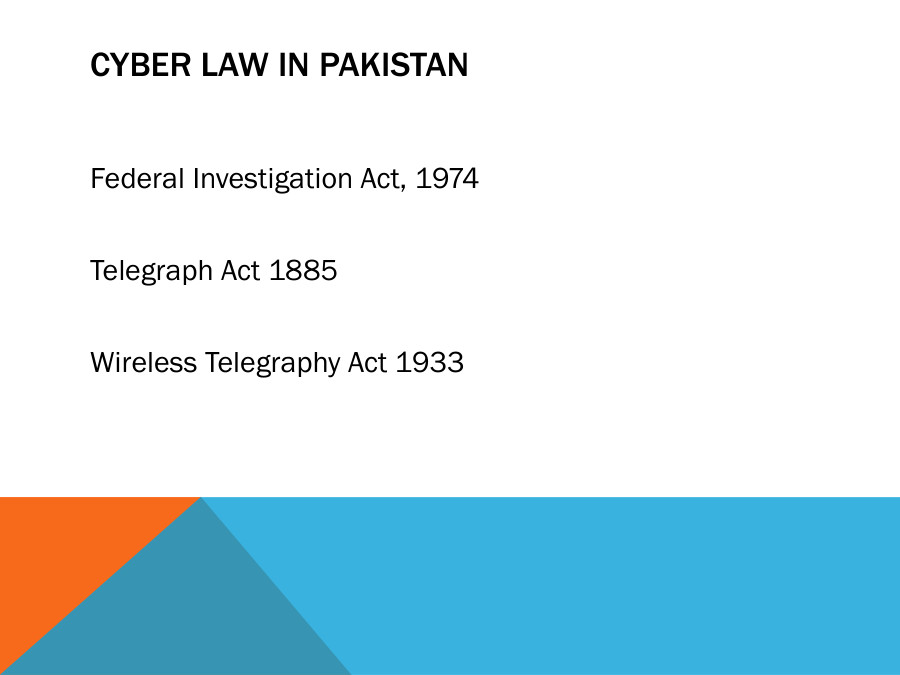






Use of a computer as an instrument to perform an illegal act, committing fraud, trafficking in child pornography, Intellectual property, stealing identities, violating privacy, etc
8 years of teaching experience
Qualification: BA, LLB, MA, LLM, PhD
Teaches: Communicative English, English, Hindi, Spoken English, Contract Law, Law, Literature
